These Statements Describe a Network Server
A server is a computer built and programmed to fulfill network needs. The TCP source port number identifies the sending host on the network.

Final Examination Router Configuration Proprofs Quiz
A network administrator configures a router to send RA messages with M flag as 0 and O flag as 1.

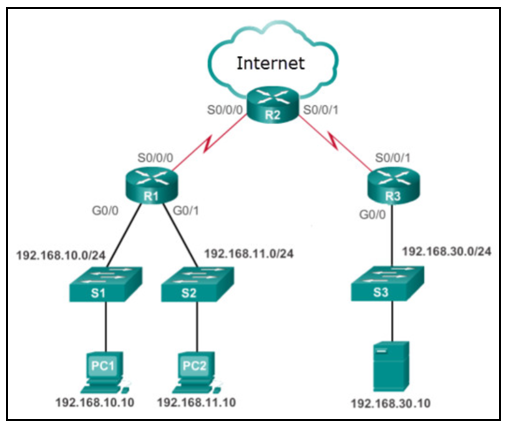
. Which statement describes the effect of this configuration. The network is administered by a single organization3The connection between segments in the LAN is usually through a leased connection4. Which three statements correctly describe the function of TCP or UDP in this situation.
It depicts the addressing scheme that is employed in the LAN. These statements describe LANs. TextIIIIstart text I I end text.
A LAN is usually in a single geographical area2. When both flags are 0 by. What term describes a network where one computer can be both client and server.
It describes whether the LAN is a broadcast or token-passing network. Which one of the following statements is true about Client-server model. Which three statements correctly describe Network Device A.
A network operating system NOS is an operating system that manages network resources. Files and folders cannot be centrally backed up. The negative consequences or impact of losing IT assets.
These statements describe LANs. Data is being sent from a source PC to a destination server. Essentially an operating system that includes special functions for connecting computers and devices into a local area network LAN.
Which statement describes the physical topology for a LAN. Search for an answer or ask Weegy. Which two statements describe characteristics of network addresses.
There are no new answers. It defines how hosts and network devices connect to the LAN. BIS 3233 Cybersecurity study questions.
To indicate whether a workstation should use SLAAC a DHCPv6 server or a combination to configure its IPv6 address. Server is a computer application that runs on. Hypertext Transfer Protocol HTTP transfers files that make up the web pages of the World Wide Web.
Select all the correct options. Telnet a terminal emulation protocol provides remote access to servers and. These statements describe LANs.
What is the main difference between a LAN and a WAN. The intentional flooding of a network or website to prevent legitimate access to. The Domain Name Service DNS protocol resolves Internet names to IP addresses.
These two flags are M flag and O flag. An event or act that could cause the loss of IT assets. Client is a computer application that runs on a server computer.
It shows the order in which hosts access the network. A network server is a computer system which is used as the central repository of data and various programs that are shared by users in a network. A network with all the nodes acting as both servers and clients A PC can access files located on another PC and also provide files to other PC.
The Simple Mail Transfer Protocol SMTP transfers mail messages and attachments. If you have a computer that youre no longer using due to its slow speed you can turn it into a network server for other computers in your household. This answer has been confirmed as correct and helpful.
The distance they span. This type of network may not be connected to other networks. Pu the networks below in order according to the geographic distance they cover.
It is used every time a computing device sends a message over the Internet. These attacks generally do not involve access to or modification of information. Does not need an expensive server as individual workstations are used to access files.
Choose three TCP is the preferred protocol when a function requires lower network overhead. The statement that describes a network server is. A condition that could cause the loss of IT assets.
Which of the following is an advantage of a peer to peer network. With a network wide mask of 255255255128 each interface does require an IP address on a unique IP subnet. Choose two A statically assigned IP address will be valid on any network to which the device connects.
It is the only protocol used in Internet communications. Which best describes a peer to peer network. The MAC address of a device will change when that.
Client is a computer application that runs on a remote computer. December 18 2014 at 545 pm. Network security can be carried out centrally.
TextIIstart text I end text. Log in for more information. Denial of service DoS attacks prevent legitimate users from accessing resources and services.
TACACS Terminal Access Controller Access Control Server - Encrypts all the information thats sent between the client and the server. With a network wide mask of 255255255128 each interface does not require an IP address. Instead they pose a threat to data availability.
30 Questions Show answers. RADIUS Remote Authentication Dial-In-User Service - Uses different network technologies to authenticate or implement authentication. Which of these statements about the Internet Protocol IP are true.
The type of network Merediths business is most likely using is a __. The NOS manages multiple requests inputs concurrently and provides the security necessary in a multiuser environment. What are the different types of cybersecurity threats.
A cybersecurity exploit is ______. According to the statement aboveWhich network architecture is that. Local-area Network LAN is a computer network that spans a relatively small area.

Ccna 1 V7 0 Modules 1 3 Exam Answers Ccna6 Com


Comments
Post a Comment